Outcome:
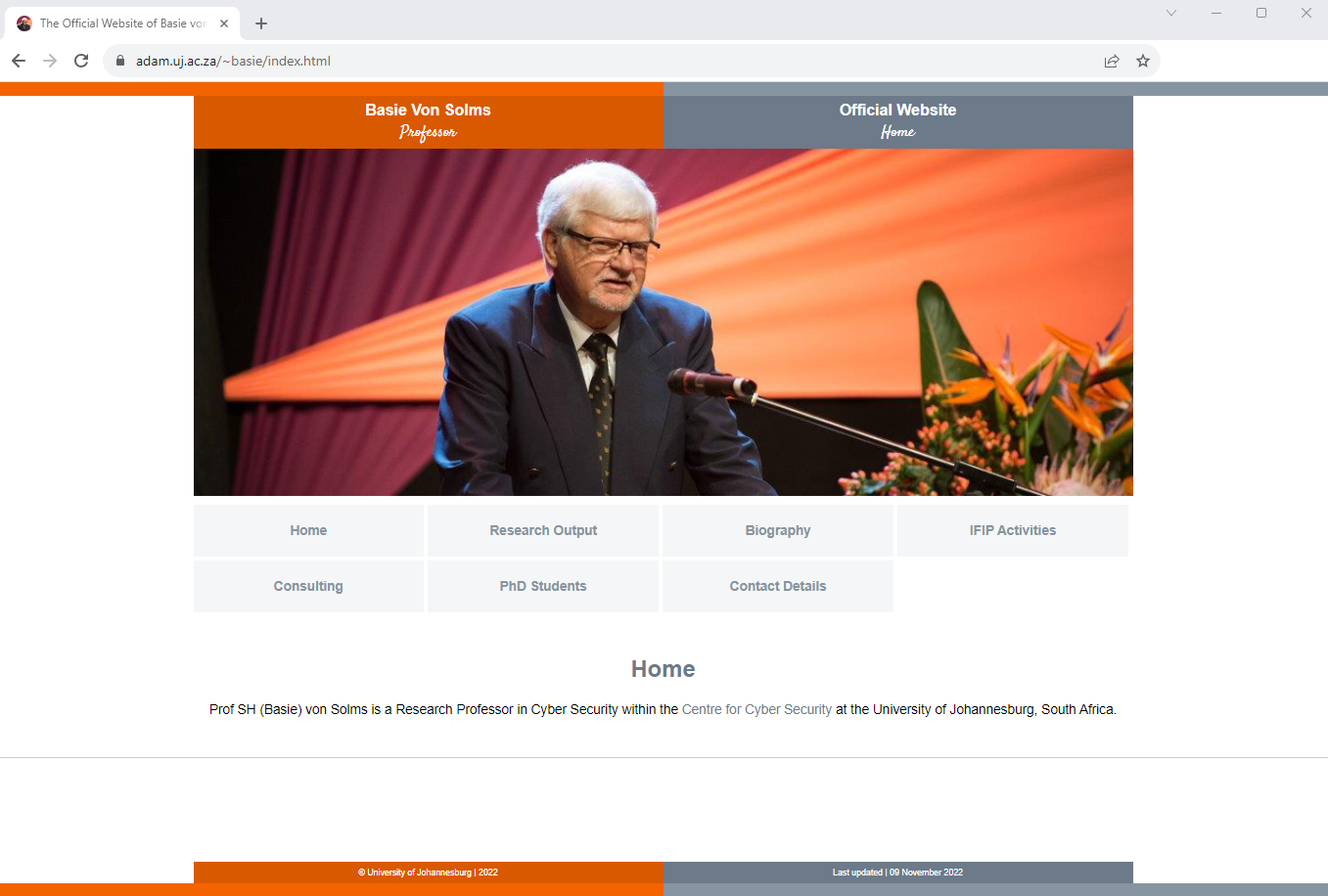
The new portal (HTML, JS, CSS, Google Analytics, Python) underwent refinement after iterative feedback rounds from the Centre Director, an external expert in the field, a local academic lecturer and a selection of end users/students.
After the approval and introduction of the new portal in 2014, the total number of page views increased steadily.
1 January 2013 – 1 January 2014: 4161 page views (old portal);
1 January 2014 – 1 January 2015: 7200 page views (new portal introduced);
1 January 2015 - 1 January 2016: 15329 page views (new portal in full production and being optimised).
Web analytics tools were also employed to provide further insight to the most popular search terms that referred users to the portal. During the year 2015, the top three searches included “security courses”, “cyber security courses” and “it security courses”. Consequently, an emphasis was placed on the development and timeous delivery of content relating to the various security courses, as well as supporting metadata (for Search Engine Optimisation purposes), with classes having burst at the seams as a result.
Unsurprisingly, the webpage containing the information on the various courses on offer attracted the biggest number of visitors throughout the year with certain weeks preceding registration deadlines sometimes having exhibited a more notable increase in visitors.
From 1 January 2013 to 1 January 2016, a vast majority of portal visitors (74%) originated from within South Africa followed by visitors from the United States of America (5%) and Kenya (4%). During this same time, more than 26 000 webpage views had been recorded of which 71% were from desktop machines, 23% from mobile devices and 6% from tablets. In 2018, a few cosmetic changes were made to the portal's banner and menu layout. In 12.2023, this design is still in use.
Note:
This information is presented as an exerpt from our published case study article: Louw, C and Von Solms, SH. (2016). Building Cyber Knowledge through Online Portals - A Case Study. International Conference on Business and Cyber Security (ICBCS), 12-13 May 2016, London, UK. ISSN 2047-2854 (Print) | ISSN 2047-2862 (Online).